Day 2 Homework: (due before the start of class November 9th) Answer the following in one or two sentences and add the information to your notes:
Vulnerability/Patch Questions: Resources: cve-details.com, OSVDB.org, and exploit-db.com
- What is a CVE #?
- Common Vulnerabilities and Exposure
- How is a CVE structured/defined/scored?
- Vendor, product names and version numbers.
- How do you search for a CVE by name? Provide an example via screenshot.
- You can search by product, vendor or version. For example
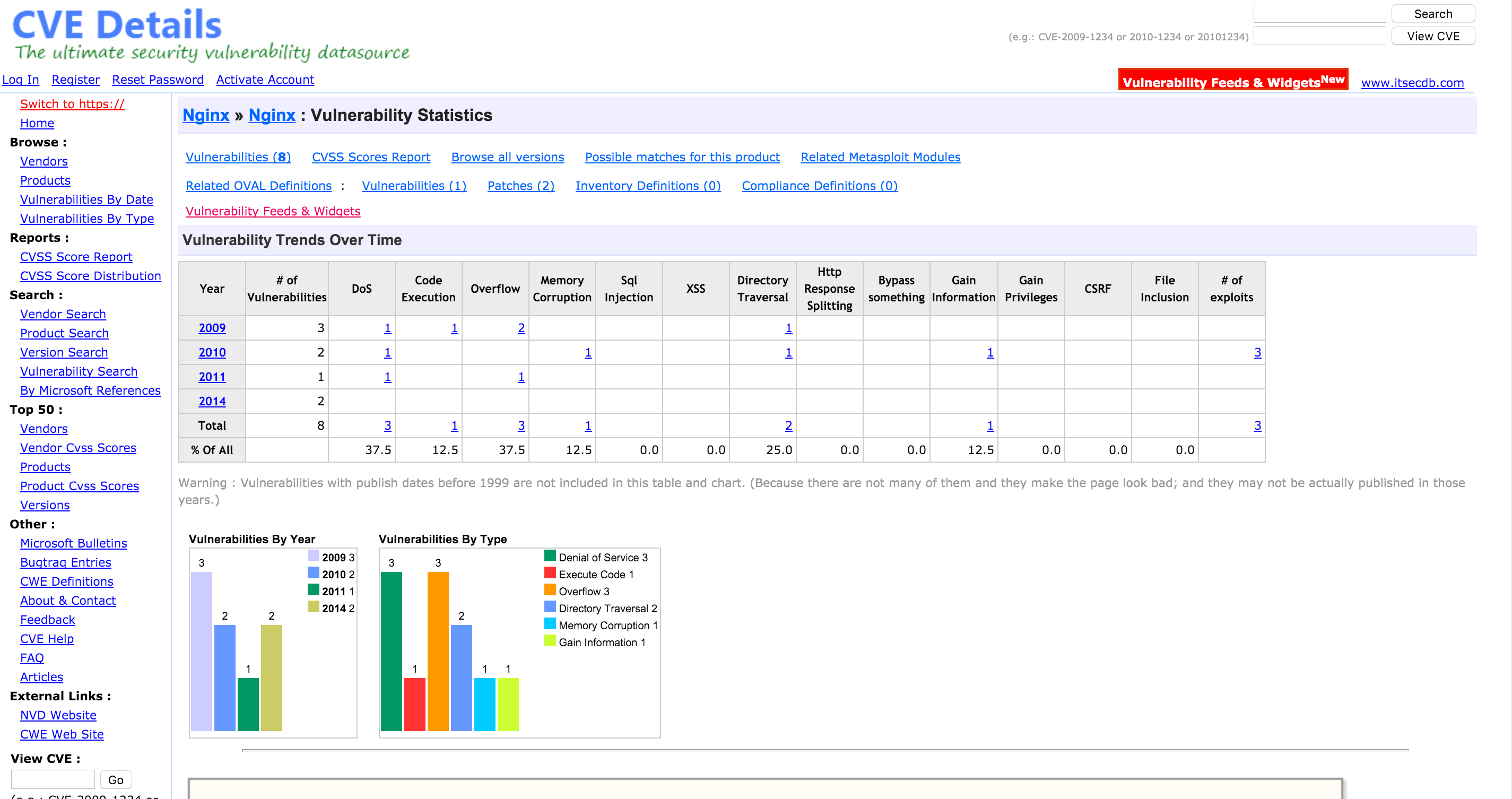
- You can search by product, vendor or version. For example
- How do you search for a CVE by #? Provide an example via screenshot.
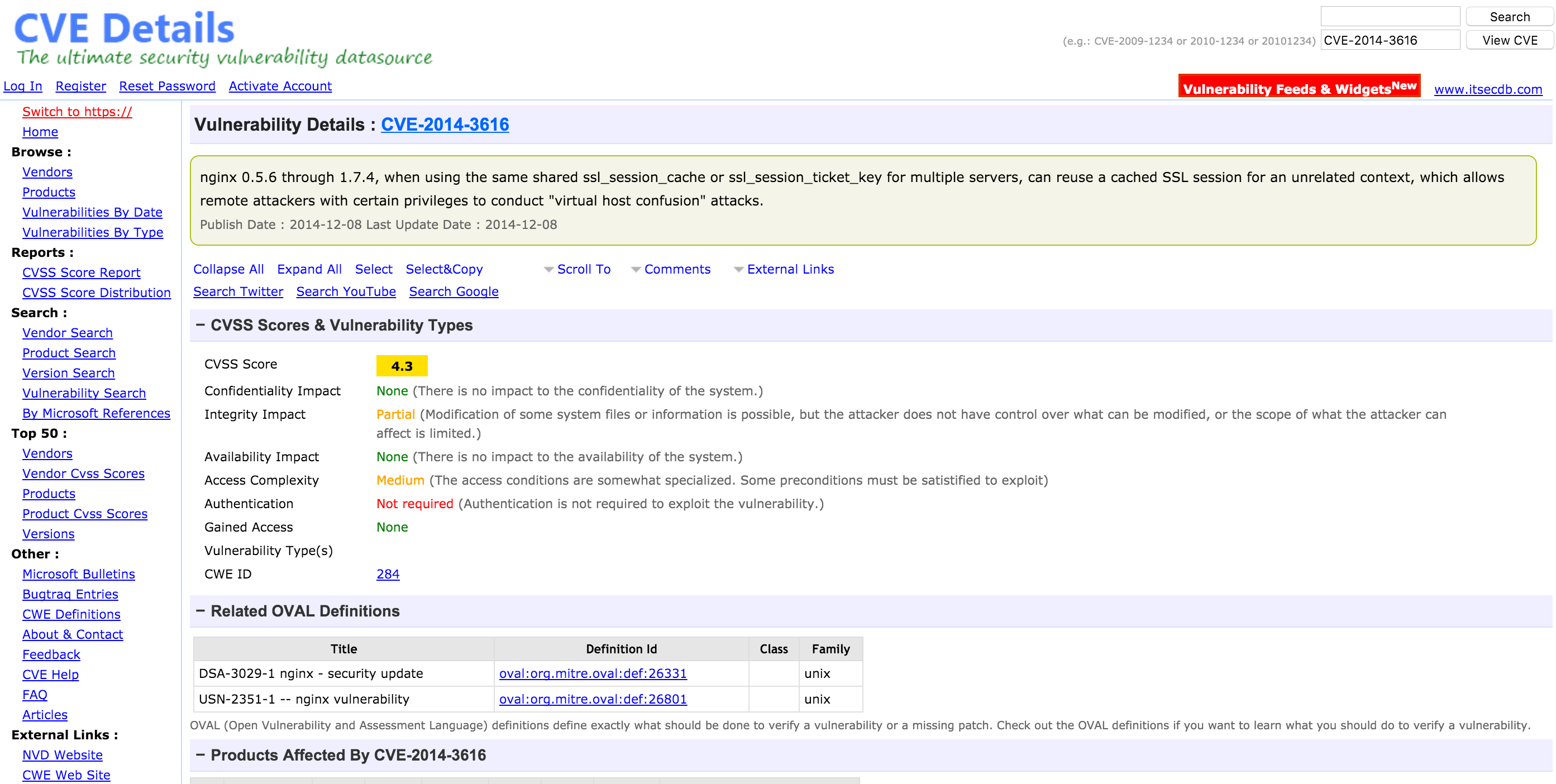
- How is a CVSS(v2) score assigned?
- https://www.first.org/cvss/v2/guide
- Composed for 3 metric groups: base, temporal, environmental
- base and temporal metrics are specified by vulnerability bulletin analysts, security product vendors, or application vendors.
- What is the CVSS rating criteria?
- a series of equations that combine three metric groups: base, temporal, environmental.
- What is a security BID #?
- Where would you find a BID?
- http://www.securityfocus.com/bid
- How is a BID associated to a CVE?
- security focus maintains BIDs and references the CVE. e.g http://www.securityfocus.com/bid/77209/info
- What is a Microsoft Security Bulletin?
- a microsoft website that tracks vulnerabilities in microsoft products.
- How does a MS Security Bulletin relate to a CVE?
- CVE appears to be more of an open standard where MS Security Bulletin seems to be focused on microsoft products and have their own standard identifier.
- What is a Microsoft security KB (Knowledge Base) Article and how does it relate to a security bulletin?
- the knowledge base article includes additional information about a security bulletin such as how to apply the patches and what versions of the product are affected.
- Provide a link the the cve-details.com page listing all vulnerabilities for Apache Tomcat version 6.0.29
- https://www.cvedetails.com/vulnerability-list/vendor_id-45/product_id-887/version_id-100326/Apache-Tomcat-6.0.29.html
Describe the vulnerability associated with MS08-067
- What is the vulnerability title?
- What is the severity rating?
- Critical
- What is the impact?
- Remote Code Execution
- Provide a quick summary of what systems are affected?
- Windows 2000
- Windows XP
- Windows Server 2003
- Windows Vista
- Windows Server 2008
- What is the associated CVE #?
- What is an associated KB patch for Server 2003?
- https://support.microsoft.com/en-gb/kb/958644
- What is an associated KB patch for Windows XP?
- https://support.microsoft.com/en-gb/kb/958644
- What is an associated Metasploit exploit for it?
msf > search ms08_067
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
exploit/windows/smb/ms08_067_netapi 2008-10-28 great MS08-067 Microsoft Server Service Relative Path Stack Corruption
msf >
Metasploit:
Resource: https://www.offensive-security.com/metasploit-unleashed/
- What is a payload?
- What is an interactive shell?
- What is a meterpreter reverse shell?
- What is a meterpreter bind shell?
- Try exploiting the vulnerability again with a meterpreter bind shell.
- How could a firewall impact a bind shell?
- it could block incoming connections
- Disable the firewall and try running the bind shell again.
- What does the command “show payloads” do?
- Running ‘show payloads’ will display all of the different payloads for all platforms available within Metasploit.
- https://www.offensive-security.com/metasploit-unleashed/msfconsole-commands/
- What does the command “show options” do?
- display which settings are available and/or required for that specific module.
- What does the command “show targets” do?
- see which targets are supported. e.g windows 2000, windows 2003 universal
- What does the command msfupdate do?
- update the metasploit database to get the latest.
- What exploits/techniques does the meterpreter command “get system” use?
- escalate the current session to the SYSTEM account from an administrator user account.
- https://www.rapid7.com/db/modules/post/windows/escalate/getsystem
- How do you specify a single technique from get system?
$ getsystem -t <option> - For the command “hashdump” to be successful, what permission level do you need?
- run as SYSTEM